Wireshark is an open source, free network packet analyzer. It captures packets in real time and lists them in a user friendly GUI with options to color code, filter and much more. It is a defacto GUI tool to monitor network traffic and can be considered astcpdump with GUI front end and integrated sorting and filtering options. If you find it interesting to read on its history, the wikipedia page should be helpful.
We’ll just look into a few of it’s aspects and capabilities now.
- Getting Wireshark
As mentioned earlier, it’s a free open source tool. So you can freely download and install on your system from its official download page and is available for windows, Mac OS X and Linux distributions. On Ubuntu, you can install it from the command line:
sudo apt-get install wireshark
- Run
Run Wireshark with root provileges. This is important!
gksudo wireshark
- Wireshark Window
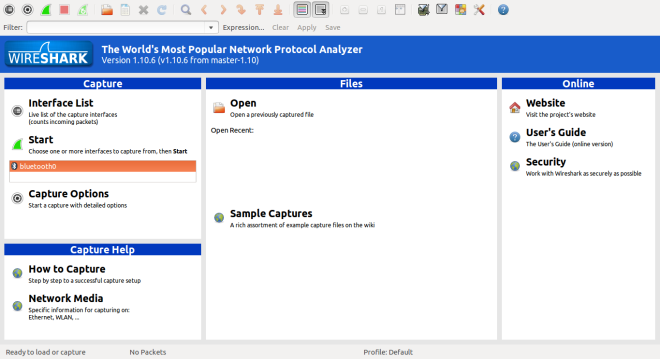
Wireshark Window Upon starting wireshark as su, the main window displays the interface list. The interface list displays the available network interfaces in the system, with options to start the capture. Capture options dialog will help you to specify various options to follow during packet capture.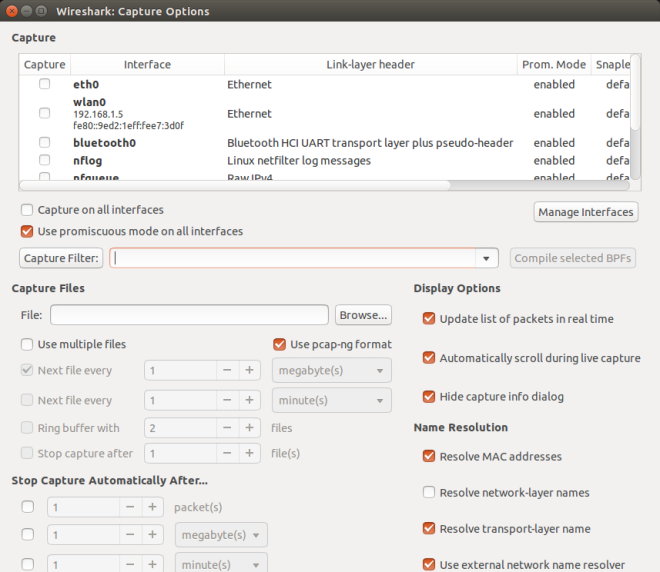
Capture Options Window - Capture Window
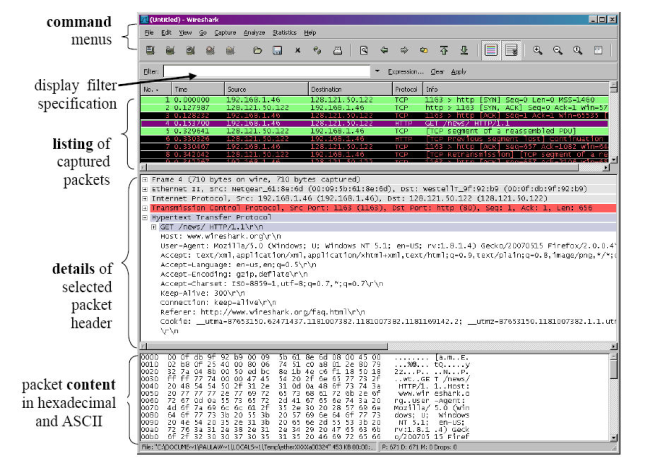
Capture Window The Capture Window as shown above displays the captured packets in real time. You can inspect each packet’s content, by choosing the appropriate packet from the packet list, in the packet details and packet bytes sections. Packets can be color coded for each protocol, filtered according to various filtering parameters and sorted on various fields. - Start Packet Capture
To start packet capture for a desired interface, you can select that interface and simply click on the start button. The Capture Window will appear showing real time captured list of packets. - Apply Filter
You can use the filtering option to filter and display captured packets according to some criteria. Appropriate filtering options can be specified into the filter box in the filter tool bar. An example criteria can be to display packets send from a particular ip(say 10.20.30.40). The suitable filtering option here will beip.src == 10.20.30.40 - Save and Load Capture Data
The captured packets can be saved as a capture file on to the disk for later use. Save the capture with a desired file name as a.pcapngfile. Wireshark also allows to save the capture file in other packet capture file formats like pcap, libpcap, Microsoft NetMon formats. - Crack passwords
Thus, with Wireshark you can inspect the network packets. This obviously means you can open it up in the packet byte section and read them. What more do you need to read a submitted form fields? Or more specifically passwords? Try creating a localhost website with a password field and capture the packets transferred during form submit. You can easily find the submitted form fields in one of the captured packets. Now that you have succeeded to steal passwords why don’t you try it out for somebody’s facebook or gmail password? To start with, steal your own facebook password. Capture the packets and inspect them. What do you see? Yeah, that’s all about https.